Monday, May 22. 2006
Dhiraagu MMS: kung fu-ed!
Ah. Data back up disks are always nice - especially those with older snaps of work. You find things that you've totally forgotten about. Perhaps it is a photo, a document or maybe that song you used to play all the freaking time. As for me, I just stumbled across a hasty log and an interesting screenshot I had taken around mid 2005.
There is a litter of articles dedicated to Dhiraagu on my blog - there is one about their E-Bill system, another on the WWW proxy server and yet another on their WebSMS service. However, the Dhiraagu MMS service, which I recall as being officially launched in July 05, is something I haven't posted about. But now that I chanced upon this "ancient" screenshot and given that Dhiraagu has revamped their MMS website, I thought I'd share...
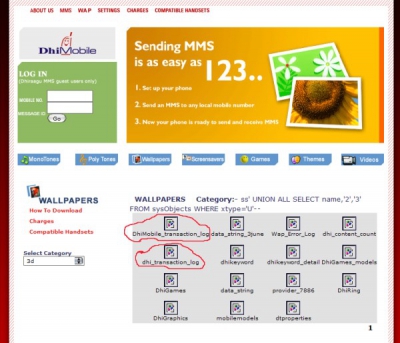
The screenshot shows the Dhiraagu MMS internet portal that is intended to be used to retrieve recieved MMS and to acquire MMS content for the phone. The shot shows an SQL injection probe on their website and listed by the system as response is a list of database tables - a couple with interesting names. I leave to your imagination what they contain, for I don't remember going pursuing any further on the matter Note that Dhiraagu seems to have re-programmed their MMS service sometime late last year and I have no idea whether the lapses that gave rise to this exploit exist on the new website.
Note that Dhiraagu seems to have re-programmed their MMS service sometime late last year and I have no idea whether the lapses that gave rise to this exploit exist on the new website.
There is a litter of articles dedicated to Dhiraagu on my blog - there is one about their E-Bill system, another on the WWW proxy server and yet another on their WebSMS service. However, the Dhiraagu MMS service, which I recall as being officially launched in July 05, is something I haven't posted about. But now that I chanced upon this "ancient" screenshot and given that Dhiraagu has revamped their MMS website, I thought I'd share...
The screenshot shows the Dhiraagu MMS internet portal that is intended to be used to retrieve recieved MMS and to acquire MMS content for the phone. The shot shows an SQL injection probe on their website and listed by the system as response is a list of database tables - a couple with interesting names. I leave to your imagination what they contain, for I don't remember going pursuing any further on the matter