Dhiraagu E-Bill flaw!
I came back from shopping this evening to find that my brother had messaged me on MSN Messenger saying he wanted to talk to me about something quite urgently. I called him up only to find him answering on the first ring and then unloading a megaton worth of speech in under a minute. He sounded excited and mostly illegible so I took my time digesting what he was saying. Basically what he said was that he had been checking the monthly call details of our home line when he got curious and took a look at the Dhiraagu E-Bill system to see what goes on under the skin. What he found was more than intriguing and he wanted me to investigate it further. (My brother has a bit of what he found out on his blog.) Now, here's my take on it.
Overview
The flaw Jaheen stumbled across lies in the online phone records viewing facility called E-Bill provided by Dhiraagu. Specifically, the flaw exists in the bill downloading section of this online application that allows registered users to download the call records for their line. The lapse in appropriate security measures and the utmost trusting of the data provided by the user seem to let a (malicious?) user view the call details for ANY account number of a Dhiraagu customer.
Walk-through
First, I should note that in order to access and execute the flaw, you need to be a registered user of the E-Bill facility. You need to log in and have a valid session underway to access the required bill downloading facility.
That said, viewing the bill of a specific user is not that trivial a task either. The account number of the desired customer needs to be provided to the system instead of merely providing the customer's telephone number. The account number is printed on the monthly bills that Dhiraagu sends out. The account number is printed in the format XX/XXXXXX/XXXX, where the Xs represent digits. Individual user targeting is thus limited greatly but this is not to say that the consequences of this bug are thus insignificant. It is always possible to mess around and generate a combination of digits which in turn will quite likely correspond with a valid account number of some random customer. A very possible scenario could be an attacker generating all the combinations of the numbers and asking for the bills for each of these generated account numbers!
I duplicated the execution of the flaw using the same "tools" my brother used; i.e. using the Live HTTP Header extension for Mozilla Firefox. This extension is quite handy for these sorts of uses and misc. other debugging purposes.
Forging ahead, first up the E-Bill interface is accessed and login process completed. This gives a cheesy interface that looks like this.
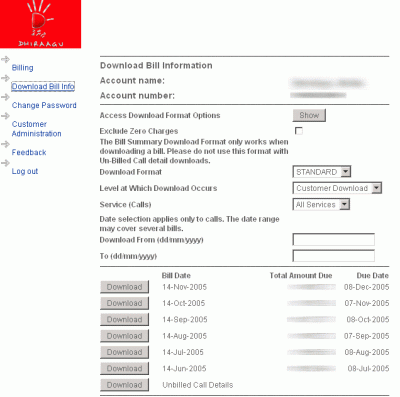
The bills download feature is accessed by clicking on the "Download bills" link from the left menu. The page that comes up next differs depending on the E-Bill account type and the number of telephone numbers combined into the E-Bill account that was logged in with. Skipping ahead, the E-Bill system throws up a page that looks like this:
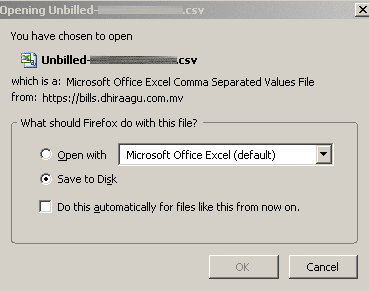
Now this is where the magic begins. Enter the time duration for which the call records are desired. The select the appropriate links to get to a download page where you are asked to click a button to start the downloading. HTTP Live Header (HLH) extension comes into play at this point. HLH is set to capture the traffic. Then the download button is clicked and soon enough Firefox happily displays the download save dialog for the file being received. The file is saved but there is nothing abnormal till this point still.
Now to execute the amazing rabbit-out-of-hat magic of the E-Bill system, a bit of sleight-of-hand is added the process. The button click in the above mentioned download process creates a HTTP POST request which shows up among the last on the status window of HLH. This request is selected and the "Replay" button clicked to replay the download process with a few changes for the final effect.
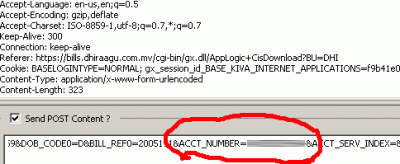
As shown above, the highlighted "account=xxxxxxxxx" bit tells the E-Bill system which account number to generate the call records for! This is where our opportunity comes. This number is then changed to a known account number or any random number and the HTTP "replay" continues as normal. Soon as the modified request is replayed, the E-Bill system again spits out a call records file for download. The difference this time? It is no longer the call records for the logged in account but for the account number furnished in the modified replay.
Conclusion
Simply by manipulating a single 12 digit number that the E-Bill system trusts the user?s browser with, we can extract the phone records of ANY Dhiraagu customer. This is a serious flaw and the resulting breach of privacy is a major concern for customers who no doubt would want their phone usage records to be kept safe and confidential.
Overview
The flaw Jaheen stumbled across lies in the online phone records viewing facility called E-Bill provided by Dhiraagu. Specifically, the flaw exists in the bill downloading section of this online application that allows registered users to download the call records for their line. The lapse in appropriate security measures and the utmost trusting of the data provided by the user seem to let a (malicious?) user view the call details for ANY account number of a Dhiraagu customer.
Walk-through
First, I should note that in order to access and execute the flaw, you need to be a registered user of the E-Bill facility. You need to log in and have a valid session underway to access the required bill downloading facility.
That said, viewing the bill of a specific user is not that trivial a task either. The account number of the desired customer needs to be provided to the system instead of merely providing the customer's telephone number. The account number is printed on the monthly bills that Dhiraagu sends out. The account number is printed in the format XX/XXXXXX/XXXX, where the Xs represent digits. Individual user targeting is thus limited greatly but this is not to say that the consequences of this bug are thus insignificant. It is always possible to mess around and generate a combination of digits which in turn will quite likely correspond with a valid account number of some random customer. A very possible scenario could be an attacker generating all the combinations of the numbers and asking for the bills for each of these generated account numbers!
I duplicated the execution of the flaw using the same "tools" my brother used; i.e. using the Live HTTP Header extension for Mozilla Firefox. This extension is quite handy for these sorts of uses and misc. other debugging purposes.
Forging ahead, first up the E-Bill interface is accessed and login process completed. This gives a cheesy interface that looks like this.
The bills download feature is accessed by clicking on the "Download bills" link from the left menu. The page that comes up next differs depending on the E-Bill account type and the number of telephone numbers combined into the E-Bill account that was logged in with. Skipping ahead, the E-Bill system throws up a page that looks like this:
Now this is where the magic begins. Enter the time duration for which the call records are desired. The select the appropriate links to get to a download page where you are asked to click a button to start the downloading. HTTP Live Header (HLH) extension comes into play at this point. HLH is set to capture the traffic. Then the download button is clicked and soon enough Firefox happily displays the download save dialog for the file being received. The file is saved but there is nothing abnormal till this point still.
Now to execute the amazing rabbit-out-of-hat magic of the E-Bill system, a bit of sleight-of-hand is added the process. The button click in the above mentioned download process creates a HTTP POST request which shows up among the last on the status window of HLH. This request is selected and the "Replay" button clicked to replay the download process with a few changes for the final effect.
As shown above, the highlighted "account=xxxxxxxxx" bit tells the E-Bill system which account number to generate the call records for! This is where our opportunity comes. This number is then changed to a known account number or any random number and the HTTP "replay" continues as normal. Soon as the modified request is replayed, the E-Bill system again spits out a call records file for download. The difference this time? It is no longer the call records for the logged in account but for the account number furnished in the modified replay.
Conclusion
Simply by manipulating a single 12 digit number that the E-Bill system trusts the user?s browser with, we can extract the phone records of ANY Dhiraagu customer. This is a serious flaw and the resulting breach of privacy is a major concern for customers who no doubt would want their phone usage records to be kept safe and confidential.