Thursday, September 21. 2006
Open routers at Dhiraagu hotspots?
Dhiraagu Wifi hotspot is something I had mentioned in an earlier post, however, I hadn't got a chance to experience the service on my laptop till recently. The opportunity popped up when my flight to UK got delayed and had to kill some time at the food outlet at the airport. My laptop readily found the "Dhiraagu Wireless Hotspot" SSID and a stable connection was established. The service was quite decent and I could browse and download in comfort and with speed. It certainly was a luxury that quite a few people would happily pay for.
As ever, curiosity got the better of me and I decided to peek a look at how the service was operating. Access controlled wifi hotspots usually operate by allowing unprotected (that is WEP/WPA free) access to the wireless network and then authenticating the client with a central access controller. The client needs to open a web page, any page, upon which the browser gets redirected to a service login page where the user is prompted to enter the login details that grant them access to the internet thereafter. The login mechanism also serves as a means to facilitate billing.
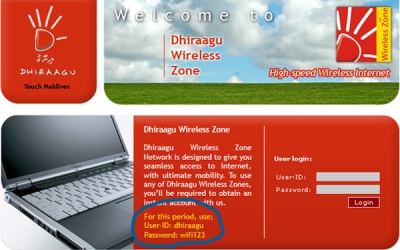
The Dhiraagu system operates in a similar manner. Below is the screen that we are shown upon connecting. Notice that they are giving the username/password to login with in the current free access promotion they are running.
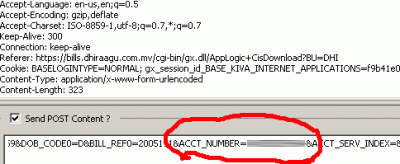
The browser flickers as the system guides it through a series of links to complete the authentication. Looking at the URLs that the browser hit through, I picked one "interesting" looking IP...
http://202.1.201.230:8002/Portal?NMIP=203.104.25.251?OS=http://www.msn.com/
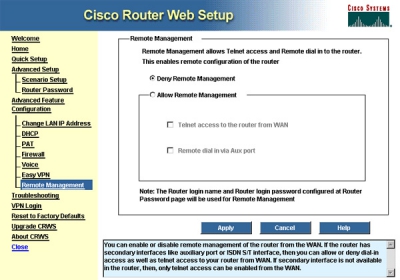
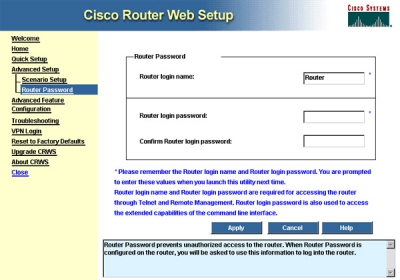
And voila comes the web administration interface for a Cisco router - the equipment that Dhiraagu is using to provide the Wifi hotspot service!
The router apparently is configured without any administration password and the act of going to the router's IP address provided unfettered access to the wifi router and hence control over the wifi hotspot service.
I wonder if this is true for all the rest of Dhiraagu hotspots splattered across Male'. The service is great, BUT is this how the system was deployed? This configuration of the wifi hotspot lets anyone command control over the router and facilitates all kinds of mischief!
As ever, curiosity got the better of me and I decided to peek a look at how the service was operating. Access controlled wifi hotspots usually operate by allowing unprotected (that is WEP/WPA free) access to the wireless network and then authenticating the client with a central access controller. The client needs to open a web page, any page, upon which the browser gets redirected to a service login page where the user is prompted to enter the login details that grant them access to the internet thereafter. The login mechanism also serves as a means to facilitate billing.
The Dhiraagu system operates in a similar manner. Below is the screen that we are shown upon connecting. Notice that they are giving the username/password to login with in the current free access promotion they are running.
The browser flickers as the system guides it through a series of links to complete the authentication. Looking at the URLs that the browser hit through, I picked one "interesting" looking IP...
http://202.1.201.230:8002/Portal?NMIP=203.104.25.251?OS=http://www.msn.com/
And voila comes the web administration interface for a Cisco router - the equipment that Dhiraagu is using to provide the Wifi hotspot service!
The router apparently is configured without any administration password and the act of going to the router's IP address provided unfettered access to the wifi router and hence control over the wifi hotspot service.
I wonder if this is true for all the rest of Dhiraagu hotspots splattered across Male'. The service is great, BUT is this how the system was deployed? This configuration of the wifi hotspot lets anyone command control over the router and facilitates all kinds of mischief!