Dhiraagu
WebSMS has been a dear friend to a lot of us. Some of us see it as a means of communicating with friends cheaply when we are strapped for cash while some others use it for more malicious purposes. Anyway, I took a different interest in it since its introduction some years ago.
Once upon a time...
When WebSMS was introduced, Dhiraagu relied on the interface scripts provided by Comverse for their SMS system purchased from
Comverse. One part of the web interface had minor changes brought to sport Dhiraagu logos and copyright lines and was offered to the public as WebSMS. It was free for use and had no limits and no Dhiraagu signature lines appended. It was total fun! Ofcourse the fun was just beginning and I forayed into the scripts and ended up with access to the rest of the system that "websms" was actually part of... Dhiraagu then started to bring changes. I suspect these changes were politically influenced rather than being for their own financial or technical reasons.
First, Dhiraagu had a signature line appended to messages. The message was easy to get rid of by merely modifying the form data being submitted to the server. Ofcourse, Dhiraagu fixed it (sorta) in due time.
Next up, they decided to add user registration. It was still free thankfully. This was the first in a step of moves they've made to gather more and more specific data on the users. This initial user registration allowed anyone with an email address to open an account. This ofcourse meant, you can use throw-away free emails and aliases to open WebSMS accounts without revealing any real info on yourself.
Then few months later, the registration with email addresses was scrapped and people were required to have a mobile number to register. The old accounts were ofcourse purged after this change. This new change ruled out random people opening accounts and sending SMS - you needed to be their customer to send SMS via the web.
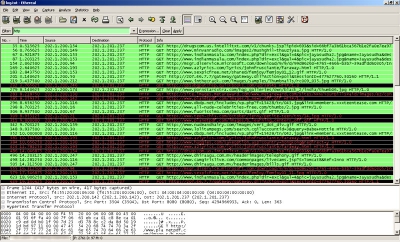
Sometime late 2004, they decided to limit the number of SMS to 10 per day per account. Now to implement this, they used a messed up implementation of sessions and cookies. When you login, you got assigned a cookie that set a key "Dhi" with a value of the form "12345%2cWanker%2cWho". Simply by altering the "12345", which is probably something meant to act as a session id, one could override the 10 SMS per day limit. By changing this value, you effectively assume the identity of another user - but all without any authentication! Simply change the number and you are good for another 10 SMS. Interesting thing was that user/session id didn't need to exist on their server - you could very well use 1000000 and move onto 1000001, 1000002 and so on for more SMS. I had the pleasure of getting my server blocked/ignored by Dhiraagu after I added this 'hack' to my Email2SMS service offered at the time via maldivianunderground.net - but the block wasn't placed until after my Email2SMS service had dispatched around 2000 SMS total using the 'hack' by the second/third day after they brought the "upgrade".
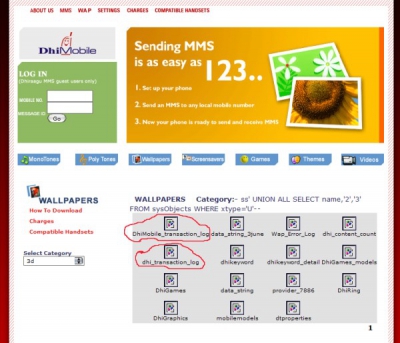
I should mention there were other interesting but less trivial flaws in the WebSMS system - like being able to reset the password for (all) users on the system via SQL injection. The database table they had, had the following fields (amongst others) : userid, username, password, mobileno. The login and password change facilities had SQL injection and logic deduction possibilities...
Soon after the 10 SMS limit "upgrade", in May 2005, Dhiraagu made another of its upgrades to make the messages that were being sent via the system seem to originate from the number of the WebSMS account holder. Uptil then, the originating number was "+000". This new upgrade killed the anonymity of messages being recieved by a WebSMS recipient. It killed the fun ofcourse and I had to find some way to get around it - just to piss off friends. It turned out Dhiraagu had simply appended the account holder's number to the cookie that is set when a user logins - and then uses that number from the cookie to represent the originating number whenever a SMS is sent. If you are having a hard time imagining how it looked, the cookie was of this form: Dhi=12345%2cJawish%2cJaa%2c770000. This opened up new possibilities! I could make SMS appear to originate from any number. I could make it that of a friend's or foe's. I could make the number an international one or even a landline one. Seeing my dad stare at the phone in disbelief when he received an SMS from himself was fun enough! Hehe.
Sadly, these "features" were fixed when Dhiraagu upgraded the system yet again in August 2005. No wild originating fun for now. I haven't messed around with it yet - much.
Psst. Tricks!
To finish off this lengthy post on Dhiraagu WebSMS, I'm sharing two neat tricks that you may like and still works on Dhiraagu WebSMS as of today.
No signature line: Don't want the "(Dhiraagu WebSMS)" line to appear in messages you send via the WebSMS system? Then simply add a equal sign ("=") as the last character in your post!
Long messages: Do you have some looonnggg message to send to someone and it's hard to fit in the 140 character limit that WebSMS imposes on you? Worry no more. You don't need to split the message into bits and send as separate messages and risk decreasing that dreaded 10 SMS limit you have for the day. All you need to do is disable JavaScript support in your browser temporary (It is an easy feat - consult your browser documentation on how to do this). When you type in the messages now, the limit counter will stay the same and you can go on typing forever. The messages are sent to the recipient as discrete SMS messages of text limit ~140 characters each. However, you will be penalized for only one SMS in the WebSMS daily limit counter.
Enjoy!
Update (14 Oct 2005): Dhiraagu has fixed the bugs that made possible the two tricks revealed above. Too bad